
There are two sorts of people in the world; those who know they are stupid and those who think they are clever. Stupid people use a password manager. They know they can't remember a hundred different passwords and so outsource the thinking to something reasonably secure. I'm a stupid person and am very happy to have BitWarden generate and save fiendishly complex unique passwords which are then…
Continue reading →

Terminology is hard. Computer terminology is even harder. Humans are animals who just love to classify things. We have a fundamental need in our delicious meaty brains to put things into conceptual buckets. This, I think, leads to some unfortunate consequences when our categories don't match up with other people's categories. For example, take this news story and this journalist's response to…
Continue reading →

There's a disturbing article in The Guardian about a person who was on the receiving end of a successful cybersecurity attack. EE texted to say they had processed my sim activation request, and the new sim would be active in 24 hours. I was told to contact them if I hadn’t requested this. I hadn’t, so I did so immediately. Twenty-four hours later, my mobile stopped working and money was wit…
Continue reading →

Some ideas are timeless. Back in 2004, an anonymous genius set up "FobCam". Tired of having to carry around an RSA SecurID token everywhere, our hero simply left the fob at home with an early webcam pointing at it. And then left the page open for all to see. Security expert Bruce Schneier approved of this trade-off between security and usability - saying what we're all thinking: Here’s a guy w…
Continue reading →

There's a new Web Standard in town! Meet WebMonetization - it aims to be a low effort way to help users passively pay website owners. The pitch is simple. A website owner places a single new line in their HTML's <head> - something like this: <link rel="monetization" href="https://wallet.example.com/edent" /> That address is a "Payment Pointer". As a user browses the web, their browser takes …
Continue reading →
Because I'm a massive nerd, I actually try to read specification documents. As I've ranted ad nauseam before, the current TOTP spec is irresponsibly obsolete. The three major implementations of the spec - Google, Apple, and Yubico - all subtly disagree on how it should be implemented. Every other MFA app has their own idiosyncratic variants. The official RFC is infuriatingly vague. That's no…
Continue reading →

The Web Crypto API is, thankfully, nothing to do with scammy cryptocurrencies. Instead, it provides access to powerful cryptographic features which were previously only available in 3rd party tools. So, is it possible to build a TOTP code generator without using any external JS libraries? Yes! And it is (relatively) simple. Here's the code that I've written. It is slightly verbose and contains…
Continue reading →

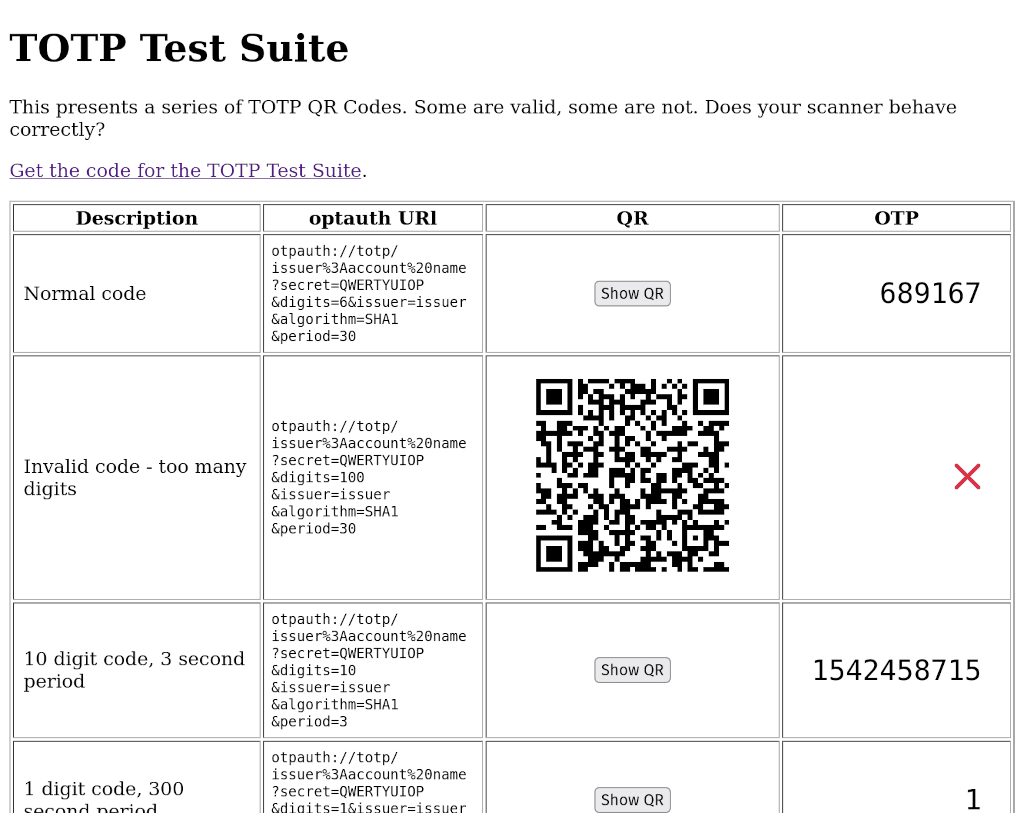
If you use Multi-Factor Authentication, you'll be well used to scanning in QR codes which allow you to share a secret code with a website. These are known as Time-based One Time Passwords (TOTP). As I've moaned about before, TOTP has never been properly standardised. It's a mish-mash of half-finished proposals with no active development, no test suite, and no-one looking after it. Which is…
Continue reading →

Android is belatedly getting a Bluetooth tracker feature which doesn't rely on proprietary apps. Long-time readers will know that back in 2016 I reviewed both the Chipolo and the TinTag. Both of those were adequate at finding things which were in range of your phone, but hopeless at finding lost items - because they required everyone to have a special app installed. But now, under pressure from …
Continue reading →

Here's a "fun" thought experiment. Imagine a website which let you sign in using only your username and TOTP code. No passwords. No magic links emailed to you. No FIDO tokens. No codes via SMS. Just a TOTP generated and displayed on your device. Is that useful? Sensible? Practical? It's certainly technically possible. Store the username, store the TOTP seed, done. Your users can now log in. …
Continue reading →

A decade ago, I appeared on the 361 Podcast to give my advice about mobile security. This was the era of the iPhone 5 and Android KitKat. BlackBerry was trying to have (yet another) resurgence and Nokia was desperately trying to keep Windows Phone alive. What advice did I give then, and is it still relevant? Stay Sceptical In at number five is just stay sceptical. I mean, quite often, lots…
Continue reading →

For lots of online accounts, a date of birth is nothing more than a very weak second factor. The majority of places aren't checking your identity, cross-referencing your birthdate, and personalising your experience based on your Zodiac sign. At most, they'll wish you a happy birthday and / or let you recover your account by providing your date of birth. But, of course, lots of people know your…
Continue reading →










